Which Danger Do Firmware Attacks Pose
Attackers can also use Option ROM attacks to alter other firmware at boot time. Unsigned firmware in WiFi adapters USB hubs trackpads and other devices can be compromised by hackers says enterprise firmware security company Eclypsium in a new report.

What Is Malware Examples Recognize And Removal
They can disrupt phone and computer networks or paralyze systems making data.

Which danger do firmware attacks pose. Code embedded in the firmware of millions of digital devices poses a serious threat to cybersecurity. In such a connected world firmware issues pose a dangerous threat to public life and privacy since devices can be hacked and made to perform actions such as random shutdowns or credential harvesting. Once in place they.
Firmware malware will exploit this lack of security by attaching their code to the firmwares code. Cyber threats are a big deal. In fact almost any firmware component can alter the boot process.
Mobile users and remote workers utilising public networks are especially vulnerable. A new feature discovered in Trickbot allows a malicious attacker to inspect the UEFI BIOS firmware of a targeted system for known vulnerabilities that have not been patched. Firmware attacks constitute some of the most high impact threats facing organizations today.
This explains that a development called Trickboot poses a significant risk to organizational and national security according to researchers at Eclypsium and Advanced Intelligence AdvIntel. In this blog were going to talk about what makes firmware so dangerous why it is so appealing to attackers and what you can do to reduce the risk. They do so by injecting malicious software into the low-level code that governs hardware prior to system boot and during runtime.
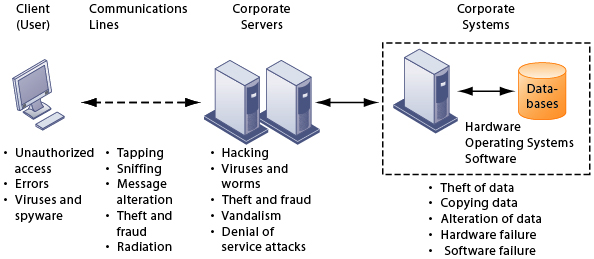
Our computers can suffer a wide variety of attacks that compromise our security and privacy. For example compromised NIC or BMC can do a DMA attack in the middle of the boot process and compromised SSD can alter the data used during the boot process bypass boot time full-disk encryption etc. Traditional Defence is No Match.
Once the malware has infected the firmware of a system it can pose a variety of dangerous threats. The following report reviews how security professionals perceive the firmware threat as well as their impression of the tech industrys readiness to detect and prevent a firmware-based attack. Once in place the rogue code can modify and subvert the firmware target OS components access high-level software and much more.
Data breaches up 17. Firmware hacks compromise a PC or device before it starts. This means that the system is rendered useless and completely inoperable.
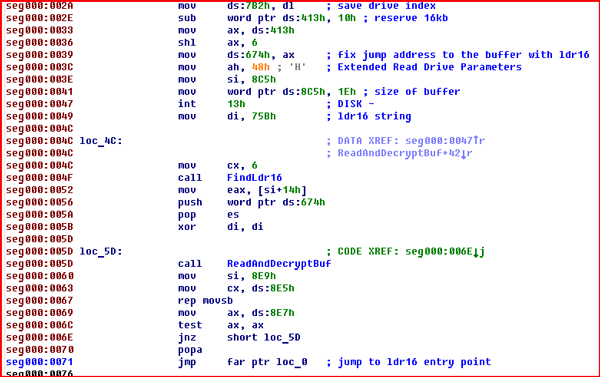
We present rmware modication attacks a general strategy that is. Because they do their dirty work deep in a systems cellar firmware hacks are hard to find. General rmware modication attack description.
Cyber attacks can cause electrical blackouts failure of military equipment and breaches of national security secrets. Techniques and embedded system malware pose a threat to the security of our existing networks we present the following four contributions. So much firmware poses a huge risk to your computer because firmware producers usually dont design their firmware with security in mind.
It is a reality that hackers can infect devices through a wide variety of methods such as fraudulent downloading fake updates email files In this article we are going to talk about firmware malwareWe are going to explain what it consists of and of course what to do to avoid being victims of. One of the most common consequences of firmware malware is that it can brick a machine. My best guess is that firmware attacks will focus more on disabling devices than modifying them to do something more sophisticated.
Over the past decade the number of firmware liabilities has increased significantly as attackers target low-hanging fruit. As seen in the previous section ransomware operators such as REvil NetWalker and others have targeted firmware in network devices as a way of gaining access and. Firmware hacks although they dont generally tend to share top billing with the likes of ransomware worms and trojans are particularly dangerous and capable of bypassing standard antivirus software by infecting the lower stack of your device.
Ransomware insider threats and attacks on firmware and hardware are growing cyberthreats reports an FBI spokesperson. The attacks can be dangerous for several reasons. Corporate IT systems will see skyrocketing numbers of cyberattacks using ransomware insider threats and vulnerabilities in firmware and hardware as sophisticated criminals seek new ways to make money according to an FBI cybersecurity expert.
They can result in the theft of valuable sensitive data like medical records. How do cyber threats pose a danger. Ransomware is one of the most pervasive and high-impact threats facing organizations today.
With control over the firmware layer attackers are able to persist on the device evade traditional security and ensure access to the highest levels of privilege on the device.

Security 101 Zero Day Vulnerabilities And Exploits Security News
Https Arxiv Org Pdf 2105 04454
Https Www Mdpi Com 2624 831x 2 1 9 Pdf
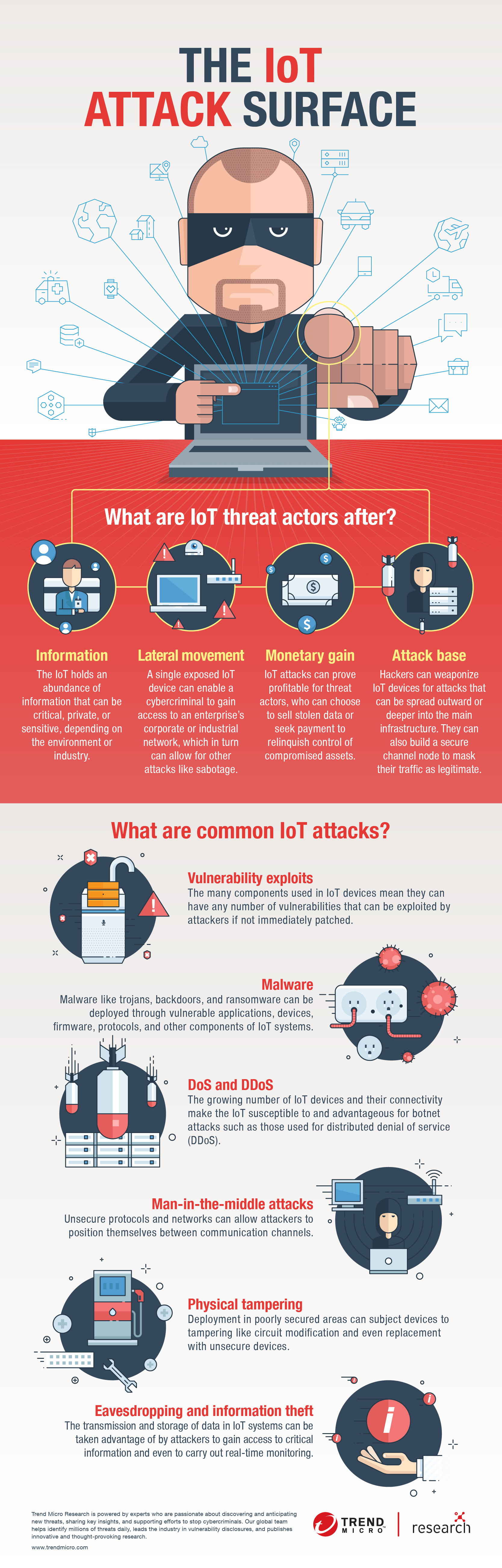
The Iot Attack Surface Threats And Security Solutions Security News

Enterprise Best Practices For Firmware Updates Security Boulevard

Vulnerabilities In Schneider Electric Somachine And M221 Plc Programmable Logic Controllers Ladder Logic Vulnerability

2017 Ddos And Web Application Attack Landscape Nsfocus Inc A Global Network And Cyber Security Leader Protects Enterprises And Carriers From Advanced Cyber Attacks

Security 101 Zero Day Vulnerabilities And Exploits Security News
Https Www Mdpi Com 2624 831x 2 1 9 Pdf
Https Www Mdpi Com 2624 831x 2 1 9 Pdf

Iot 2020 Trends And Challenges Technative Iot Voice Technology Internet Connections

The Ddos Attack On Dyn S Dns Infrastructure Ddos Attack Attack Dns

What Is Identity And Access Management Cyber Security Awareness Management Agile Project Management

New Scada Flaws Allow Ransomware Other Attacks Cyber Security Attack Flaws



Post a Comment for "Which Danger Do Firmware Attacks Pose"